WordPress security is fundamental: Every WordPress website needs to be fully secured and hardened.
“Why would a hacker be interested in my website? It’s just the website of my local business, seen by a few hundred people at most. What are they going to get out of it?”
There are many reasons why a hacker would be interested in your “small” website.
Although some hacking is done for political reasons (defacing of websites to send particular political messages, for example), these types of hacks are typically very localized and not as popular as the mainstream media would make them out to be.
Most hacking attacks happen for more devious reasons.
These days, hacking is part of a ring of criminality whose ultimate aim is to make money through fraudulent means. Typically, after a website is hacked it becomes a middle-man for the distribution of malicious software. Most times, the website owner is oblivious of all of this.
There are frameworks which are bought and sold in the online black market, making it dead-easy to distribute malware through hacked websites.
In essence, your website could become an involved party in criminal activity!
Besides that, there are other negative implications:
- Your site could be used as a spamming proxy
- A website that is hacked and defaced would most likely result in tarnishing of a brand’s reputation. That’s besides serious embarrassment
- Hacked sites typically overwhelm their hosting server, resulting in the closure of the site. This will typically result in loss of business
- The costs of recovering a hacked website can vary from very little (if you have a website backup) to a full redevelopment if your data is deleted/lost with no chance of recovery
Do you think your site is so small nobody will attack it? Think again.
Using the following WordPress security checklist will go a long way towards making your WordPress site hacker-proof.
How Does a Hacker Find My Site?
You might falsely assume that in the millions of websites available online, the likelihood of a hacker finding and targeting your site is extremely remote. After all, your site is only a drop in an ocean of websites, right?
You’re horribly wrong.
Hackers don’t do this work manually. They employ minions to do their dirty work.
Well, not really minions – they’re actually (ro)bots, or programs whose sole purpose is to seek out vulnerable websites.
These programs or scripts are typically run on cloud servers, where they can be setup and destroyed at will leaving little to no traces. The scripts employ means to discover hundreds if not thousands of websites per hour.
The fact that the scripts are bought very cheaply and run on cheap cloud hosting servers make the “investment” worthwhile. These scripts are commonly bought and sold on dodgy marketing forums.
Once a site is found, it is probed for thousands of known vulnerabilities. If your WordPress site has not been fully secured, the likelihood of the site emerging unscathed is absolutely minimal.
Vulnerabilities are continuously being discovered in WordPress and its plugins. That’s why securing WordPress is critical to the health of your website.
Securing WordPress: A 32-Step Checklist
With all of the above scary stuff in mind, I want to make sure that you’re armed with all the knowledge you can get to fully secure your WordPress website.
Here’s a checklist of ALL the things you should be doing to secure your WordPress sites.
This checklist is split into two: The first part includes measures absolutely everybody should be doing – mostly basics stuff, like having strong passwords. The second part goes into advanced measures for WordPress security for those who are really paranoid about security. This is for admins who want to lock the door, put a chain around the door, and put a padlock on it. And then a padlock on the padlock.
Part 1: The Steps Everybody Should Take to Secure Their WordPress Website
#1: ALWAYS Keep Your Version of WordPress Up-To-Date
#2: Don’t Change WordPress Core
#3: Make Sure All Your Plugins Are Updated
#4: Remove Any Inactive or Unused Plugins
#5: Make Sure All Themes Are Kept Updated
#6: Install Themes, Plugins and Scripts ONLY From Their Official Source
#7: Choose a Secure WordPress Hosting Service
#8: Make Sure Your Site is Running the Latest Version of PHP
#10: Always Use Strong Passwords
#12: Protect Your Password(s) By Avoiding Plain-Text Password Transmission
#13: Only Update Your Site From Trusted Networks
#15: Enable Google Search Console
#16: Secure WordPress With a Bulletproof WordPress Security Plugin
#17: If All Else Fails, Restore From Backup
Part 2: Securing a WordPress Website for Security Freaks
Well, not really security freaks, per se.
Although these are slightly more advanced WordPress security tips, you typically only need to know how to install a plugin, tweak a few files here and there and in general be ready for the possibility to break stuff. Be ready to revert with backups if that happens.
#19: Enable Two-Factor Authentication
#20: Ensure File Permissions Are Correct
#21: Change the Default Table Prefix
#22: Ensure You’ve Set WordPress Secret Authentication Keys
#24: Segregate Your WordPress Databases
#25: Restrict Database User Privileges
#27: Secure Your wp-config.php File
#28: Disable XML-RPC (If You Aren’t Using It)
#29: Disable PHP Error Reporting
#31: Use a Content Delivery Network Firewall
#32: Monitor Your WordPress Security With Security Logging
Part 1: The Steps Everybody Should Take to Secure Their WordPress Website
#1: ALWAYS Keep Your Version of WordPress Up-To-Date
Time and again, you hear of people who disable WordPress core updates because “an update might break one of my plugins.”
This is seriously flawed reasoning.
If you had to choose between a hacked site and a temporarily broken plugin, which would you choose?
Plugins that are incompatible with the latest versions of WordPress are only going to stay that way for a very short time. A hacked site, on the other hand, is a far bigger problem.
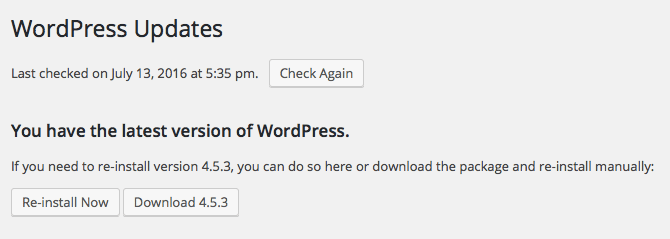
It’s important to always keep your WordPress core software up-to-date.
Each core update fixes any recently discovered security problems. If your WordPress core software is not updated, your website will be vulnerable to these problems.
If you want to enable WordPress core updates without a plugin you can do it through your wp.config.php file. Add the following line to the file:
| define(‘WP_AUTO_UPDATE_CORE’, true); |
view rawwordpress-auto-updates hosted with ❤ by GitHub
The above, however, will also enable core development and nightly updates, which you probably don’t want. Add the following to your functions.php file to only get major and minor releases:
| add_filter( ‘allow_dev_auto_core_updates’, ‘__return_false’ ); |
view rawwordpress-minor-updates hosted with ❤ by GitHub
Note: We don’t usually recommend directly editing your functions.php file. It’s always better to create a child theme.
We will discuss later on how to also automatically update WordPress plugins and WordPress themes.
#2: Don’t Change WordPress Core
The moment you or a developer edits WordPress core source files, you can no longer easily and automatically update WordPress to the latest version since you’ll lose changes you made to your site
This leaves your website dead in the water as soon as a security vulnerability is discovered in your version of WordPress. You’ll either have to figure out how to implement the specific fixes yourself, or just leave it unpatched. The former is a lot of hassle and a logistical nightmare; the latter is a serious security risk.
What should you do if you need to change WordPress functionality? Write a plugin of course. This gives you the ability to do whatever you need without compromising WordPress core.
Of course, the same logic applies to plugins and themes. The moment you perform any core tweaking of plugins and themes you lose the ability to update to the latest version. This leaves your site open to hacking.
There are ways and means of getting the desired functionality you need without actually changing the core. If any developer you work with suggests making any such changes, run a mile.
#3: Make Sure All Your Plugins Are Updated
As with WordPress core files, vulnerabilities are frequently found in third party WordPress plugins. There have been plenty of high-profile hacking incidents due to popular plugins containing vulnerabilities.
We won’t name and shame them here. Most software is prone to these issues at some point in its existence. It’s how the vulnerability is dealt with that shows you what the people running the company are made of.
Many times, as soon as a problem is discovered the developers of the plugin will quickly fix it and release an update.
At that point, it becomes your responsibility to update the plugin to the latest version otherwise you are still prone to a hack attack.
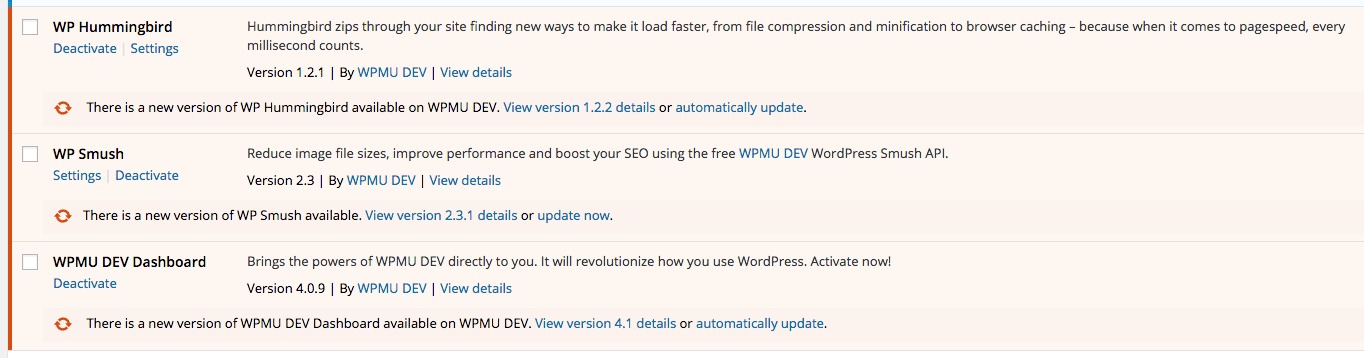
Whether you do it manually, or automatically, always keep your plugins updated.
You can enable automatic background updates on WordPress.org plugins using the following change in your functions.php file
| add_filter( ‘auto_update_plugin’, ‘__return_true’ ); |
view rawauto-update-wordpress-plugins hosted with ❤ by GitHub
This only applies to plugins downloaded from WordPress.org. Any commercial plugin updates need to be handled through their own update mechanism.
Don’t neglect the updating of plugins. Keep memberships of plugins active so that you can always get the latest updates.
#4: Remove Any Inactive or Unused Plugins
As the number of plugins you install increases, so do the risks of a vulnerability being discovered in one of those plugins.
Sometimes we install plugins to test their functionality and then forget to remove them from our site. If a vulnerability is discovered in these plugins, your site becomes a sitting duck (especially if you don’t follow the advice above and always update the plugins).
Your website is still vulnerable even if that plugin is installed on your website and not being used.
The safest way to minimize the risks is to completely uninstall any plugins you are not using. There is a very easy way to know which plugins are not being used. They are marked as Inactive in the Plugin section of the WordPress admin.
Delete them.
Also, remove any plugins that are active but still not actually being used. Better still, when testing plugins, don’t test them on your live site. Instead, create a test copy of your site (on a local test server or somewhere that is segregated from your live server). Perform any plugin testing on that site instead of your live site.
#5: Make Sure All Themes Are Kept Updated
The same logic that applies to WordPress core updates and plugin updates, applies to themes. Securing WordPress means that all themes need to be kept updated to their latest versions. Otherwise, any security holes that have been fixed will remain an issue on your site.
Now you may probably be thinking about all of the changes you’ve done to the theme and how these will break if you perform a theme update. In reality, changes to themes should be done via child themes, rather than directly to the actual theme. This will allow you to get the latest fixes and security updates without breaking your changes.
If you want to put your mind completely at rest, it would be best to also remove any unused themes. You can check which themes requiring updates from the Appearance > Themes section in the WordPress admin.
You can also enable automatic background updates for WordPress.org themes also using the following change in your functions.php file:
| add_filter( ‘auto_update_theme’, ‘__return_true’ ); |
view rawauto-update-wordpress-themes hosted with ❤ by GitHub
This applies to themes downloaded from WordPress.org.
Any commercial theme updates need to be handled through their own update mechanism. Keep your subscriptions active to ensure you get all security updates.
Note: If tweaking wp-config.php and functions.php files is not your thing, you may choose to enable all automatic background updates using the WordPress plugin, Advanced Automatic Updates. You can use Advanced Automatic Updates to tweak the settings of auto-updates and ENABLE all of the above.
#6: Install Themes, Plugins and Scripts ONLY From Their Official Source
Sometimes when times are tough we might get tempted to “bypass” the payment of a good theme or plugin, by getting it from *cough* less than reputable sites.
Actually, there’s no harm in naming and shaming here. Pirating, torrenting and other warez sites are something you need to avoid like the plague.
What we typically don’t realize, though, is that many of these pirated themes you download for free have been maliciously tweaked. Most times a back door has been installed in the script. This allows the site where the theme or plugin is used to be remotely controlled by hackers for nefarious reasons.
Would you trust your money to a known scam artist? I wouldn’t think so. Same thing for your website. Don’t trust “free” WordPress scripts coming from people whose business is stealing other people’s work.
So where are the safe sites to go to find quality themes?
WordPress.org is the most common place where plugins and themes for WordPress are found. Commercial plugins or themes can be found at many sites starting of course with WPMU DEV and sites like WordPress.com, ThemeForest.net or CodeCanyon.net
If WordPress security is important to you, stay away from pirate sites.
#7: Choose a Secure WordPress Hosting Service
A good WordPress hosting service goes a long way towards protecting your site from hacking attacks.
Security conscious hosting services will have a dedicated security team who monitor the latest vulnerabilities (even 0-day hacks, i.e. those for which there is no remedy yet) and preemptively apply rules on their firewalls to mitigate any hack attacks on your site.
WordPress hosting is a bit of a hot topic, so I won’t be making recommendations here, but the WordPress hosting page does make a few suggestions. These are by no means the only security conscious hosting companies out there. Check out post Web Hosting Review: So Just Who is the Best? for a rundown on the web hosts to look out for.
#8: Make Sure Your Site is Running the Latest Version of PHP
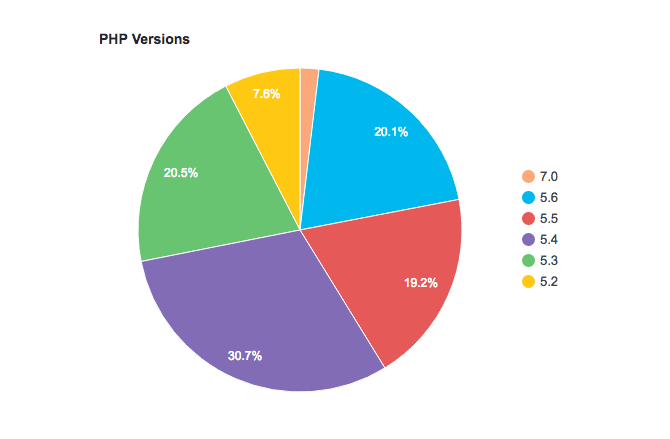
The global WordPress statistics page includes an alarming statistic: Only 1.7% of WordPress installations run on the latest version of PHP (7), whilst about 19.8% run version 5.6, which is still supported.
The rest of the WordPress installations (close to 80%) run on versions that are no longer supported!
Besides the fact your site is not benefiting from performance features released with latest versions, it also means that security fixes that are discovered will not be fixed. They will remain in the wild, ready for exploitation.
Just like WordPress gets a number of core updates, including security fixes, PHP, the underlying engine of WordPress, also gets it fair share of version updates.
Now, updating WordPress core, themes and plugins is a fairly straightforward operation.
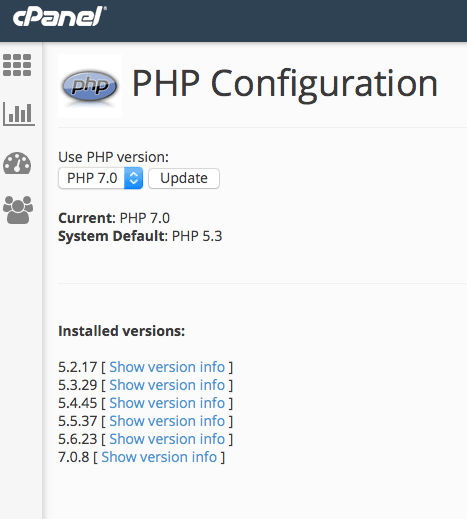
On the other hand, updating your PHP version depends largely on your hosting service. A good hosting service should make the latest PHP versions available for use with your WordPress installation through something called with PHP Version Switcher (which is typically accessed through your cPanel account).
#9: Change the Admin Username
Up until WordPress 3.0, the default user name of the administrator login was “admin.” This created a bit of a bonanza for hackers as there was no need for them to guess the administrator username. This is something still valid today. Many people still choose to use “admin” as the default administrator user name.
One of the quickest ways to secure your WordPress admin login against brute force attacks is to change the default “admin” username to something more difficult to guess. (This is what saved my own site from getting hacked).
You can – and should – do this during the actual installation of WordPress.
If your username is currently admin, you should create a new administrator user with a username that is less obvious to guess and delete the old admin user.
You can also rename the user using phpMyAdmin, or choose to run a SQL script on your database to rename the admin user:
| UPDATE wp_users SET user_login = ‘newcomplexusernameforadmin’ WHERE user_login = ‘admin’ |
view rawupdate-admin-username hosted with ❤ by GitHub
This quick and easy WordPress security trick can thwart many simple hacking attempts.
#10: Always Use Strong Passwords
When watching a client enter their administrator password, I like to give them their privacy and look away from the keyboard.
But a few years back, I accidentally didn’t look away fast enough whilst they were typing the password. To my dismay, I saw them type the following:
1 2 3 4 5 6
To say I was horrified would be an understatement.
Another login and password combination I come across very often, which (nearly) brings tears to my eyes, is this username and password combination:
admin/admin
Besides the fact that anybody looking over your shoulder (like myself) would immediately pick up that password, there is a much more serious reason why you must create strong passwords: hackers know that human beings tend to forget their passwords and are prone to using simple, easy to guess passwords.
They use this to their advantage by having a list of most commonly used passwords, which they try over and over again. This is called brute-forcing a password. Since some people WILL use these passwords, it’s essentially a numbers game – and the odds are usually stacked against you.
So always use a strong password.
Here’s an example of a strong password: ThizzI5alongstr*ngbuzzw00rd$
Should all your passwords be as complex as this one? Probably.
#11: Don’t Reuse Passwords
You should NEVER reuse passwords.
I hear you, it’s convenient to have one (hopefully strong) password across the board. You won’t have to remember so many passwords but this is very wrong on many levels.
Once again, hackers know this is a bit of a human weakness. It means that when one of your accounts is compromised they have probable access to ALL of the rest of your accounts.
There are plenty of password managers out there that will allow you to create different passwords and store them securely. These are highly recommended.
This is not just WordPress security – this is just common sense.
#12: Protect Your Password(s) By Avoiding Plain-Text Password Transmission
It’s a known fact (and a sad reality) that there is all kinds of snooping on internet traffic. Sensitive data such as credit cards and passwords should never be sent in unencrypted form.
There will be plenty of eyes (and analyzers) on your data. Do make sure you protect your passwords by employing the following preventive techniques
- Don’t send passwords over email, chat, social networks or other unencrypted forms of transmission
- Implement HTTPS on your WordPress site, particularly on your backend, to avoid passwords being sent in plain-text. You can learn all about implementing HTTPS in our article How to Use SSL and HTTPS with WordPress.
- Avoid using plain FTP when accessing your site. Use SSH or FTPS. The FTP protocol was written in the internet dark ages, and it’s not safe to use. Passwords and files are transmitted in plain text and not encrypted at all. FTPS or (Secure FTP), on the other hand, actually encrypts data transmission over FTP. You’ll need to setup an FTPS account on your hosting server before being able to do this.
- Of course, passwords should not be shared between users or stored in plain-text anywhere no matter how convenient this may be. The practice of sharing logins and passwords flies in the face of security and accountability.
#13: Only Update Your Site From Trusted Networks
Sometimes we tend to take the convenience of finding free Internet Wifi as a godsend.
But paranoid security freaks (like me) tend to shudder at the thought of updating a website from an untrusted network such as the free Wifi connection at your local cafe.
An open Wifi connection is extremely easy to snoop on. You may be getting much more than the “freebie” you thought you were getting if you access your WordPress administration site from a network that is untrusted.
Only update your site from trusted networks, such as those at your home and at your office.
#14: Use a Local Anti-Virus
Imagine you are a computer virus sitting on a desktop workstation. Bear with me for a moment.
Remember that a virus’ primary aim is to spread itself as far and wide as possible. What better way for that virus to propagate than replicating itself onto your website. That’s pretty nifty, huh?
This is a tactic widely used by viruses. There are many infected workstations out there at any point in time. And of those workstations, there are many who are being used by WordPress administrators.
That’s a bit of a worst case combination. A virus on your desktop can quickly spread itself and lead to infection of your site too. It can also snoop on your passwords and, heck, even your credit card and other personal details.
Make sure your local workstation is running a good and updated antivirus to prevent it from getting infected and spreading to your website.
#15: Enable Google Search Console
Whilst this is not a strict WordPress security recommendation, it’s something that can supplement the steps you’ve already taken to bolster your WordPress security.
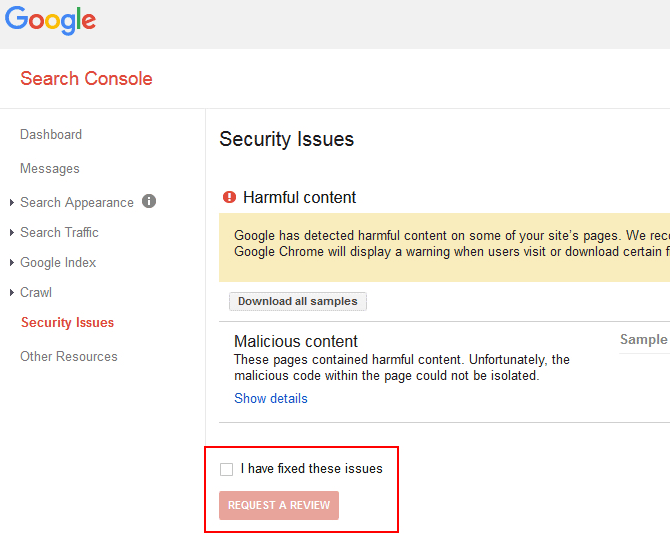
Google and other search engines have an interest in making sure your website is kept clean of malware. For this reason, the Google Search console will advise you if your website starts to host any malicious files.
Although this is a non-ideal situation where your site would have been hacked already, rather than acting to prevent your WordPress site from being hacked, it’s still good to know that malware has been detected on your site so that you can rectify the problem as soon as possible.
#16: Secure WordPress With a Bulletproof WordPress Security Plugin
Many of the steps in this checklist are not trivial. They also might require a bit of technical tinkering with your WordPress website, and rather than securing WordPress, you may blow it up.
We’ve got you covered, though. Defender is an easy but sure way of securing WordPress with little to no effort from your side. Our security plugin can identify any WordPress security issues currently affecting your websites and provide guidance on how to fix them.
Whilst, we believe that Defender is one of the best options for people familiar with WPMUDEV, there are plenty of other options in terms of WordPress security. Two of the more popular options are Sucuri and Wordfence – they are very different in the way that they work. The former is a fully cloud-based solution which also couples as a firewall and even a CDN, the latter is actually working on your site directly (it’s a plugin). We’ve reviewed both of them on CollectiveRay.com, so have a look at that article too, if you want to make an informed choice with the pros and cons of each.
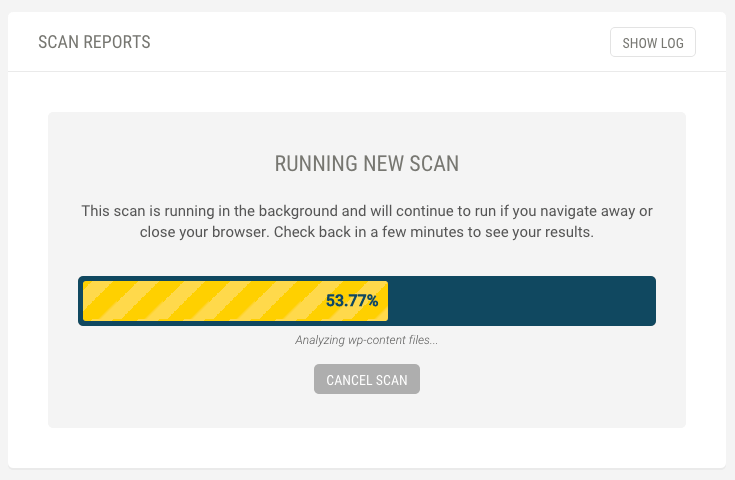
Once you’ve fixed any issues, you can also run a scan to ensure that none of your themes or plugins contain any known vulnerabilities. If they do, you’ll be able to take action to fix these issues before they become major problems for your site.
Besides the first time you install it, Defender allows you to schedule regular scans of your websites. If you’re like me, you’re bound to be very enthusiastic about WordPress security one day, but as things get busy security goes on to the backburner. Automatic scans will ensure you don’t go lax with your WordPress security.
There are plenty of other excellent features in WordPress Defender, including blacklist monitoring and alerts, vulnerability reports and customized hardening.
#17: If All Else Fails, Restore From Backup
I’ve listed quite the checklist of things you should do to secure WordPress and I do understand that it may be somewhat tasking to implement all of these. I also know that in practice, you might lapse and miss a few of them.
But there’s one task you really should not skip!
If your timing is unfortunate and your lapse happens at the same time as a hack attack, it’s important o have a fall-back plan.
The one thing you should never, ever miss or forget to do is have a WordPress backup plan. Not only in the case of hack attacks, but even in the case of accidents, technical faults and other mishaps. Having a backup ensures you can get your site back up and running again quickly.
Snapshot Pro is like a time machine for your website, enabling you to backup and restore your entire site and even schedule regular automated backups.
Once you’ve setup a backup plan, you know that if your site is hacked you just need to discover the source of the hack, revert from backup, fix the “hole” that allowed your site to get hacked and you’re good to go.
Important note: You should TEST your WordPress backup every so often by restoring it to a temporary location and making sure everything is in working order. The last thing you need is a backup that you think works, but in fact doesn’t.

Part 2: WordPress Security For Security Freaks
#18: Limit Login Attempts
We’ve already discussed brute-forcing of passwords and the fact that using bots is cheap and a good investment for hackers. For this reason, you should put in place mechanisms to block any attempts at brute-forcing your password.
The Limit Login WordPress plugin does exactly this. If it detects a number of incorrect login attempts it denies that user the possibility of trying again for some time. This, of course, makes the brute-forcing attempts much more difficult to succeed and significantly improves your WordPress security.
#19: Enable Two-Factor Authentication
One way of quickly and very easily securing your WordPress logins is by enabling Two Factor Authentication, also known as 2FA.
2FA creates a mechanism whereby to log in to your WordPress backend, besides your regular password, you will also need a time-based security token that is unique to each user. This token also expires after a period of time usually 60 seconds.
The security token is typically generated by an app such as the Google Authenticator.
Because there is a security token unique to each single user that expires, even if somebody knows your login credentials, they will still not be able to log in. This is because they will not have the current security token. This drastically increases the strength of your login and also helps mitigate brute force attacks on your login details.
There are a number of plugins that can help you setup WordPress Two Factor Authentication. Check out 6 Best WordPress Security Authentication Plugins for some of our favorites.
#20: Ensure File Permissions Are Correct
This is a bit of technical thing.
PHP and WordPress in general use a set of permissions associated with files and folders. Without going into too much detail, there are different types of permissions
- Publicly writable files and directories
- Files writable by the web server only
- Read-only files
In general, your web server typically needs to be able to write files for WordPress to work correctly, whilst the public internet NEVER needs to have write access to your files.
Some newbie or lazy developers, might suggest that you change permissions to be more lax. For example, they might suggest making certain files or folders publicly writeable (777). This will create a serious security threat because it means that anyone can write anything to that folder. You can rest assured that you’ll find plenty of nasties in your WordPress site if you do that. They will also probably find ways and means of jumping out of the folder to wreak havoc on the rest of your site.
As a general rule of thumb, files should have a 644 permission and folders should have 755 permissions. The wp-config.php file should have 400 or 440 permission.
If anybody tells you otherwise, be very wary. My suggestion is stop dealing with anybody who suggests otherwise.
How can you check for the correct file permissions? Defender, mentioned above, is a WordPress security plugin that will check and fix file permissions for you as necessary.
#21: Change the Default Table Prefix
This is another remnant of old versions of WordPress. Previously, the name of WordPress tables in the database used to start with the prefix wp_
Although this is no longer default behavior, some people still tend to revert to this (unsafe) practice, whilst older versions of course still have to live with this.
Although this is, strictly speaking, WordPress security through obscurity, renaming the tables from wp_ to a different prefix may still block some attempted SQL injection attacks.
The procedure to rename existing wp_ tables should be done only by your trusted WordPress developer.
#22: Ensure You’ve Set WordPress Secret Authentication Keys
You might have come across these eight WordPress security and authentication keys in your wp-config.php file and wondered what they are. You may also have never seen or heard about them.
They look something like this:
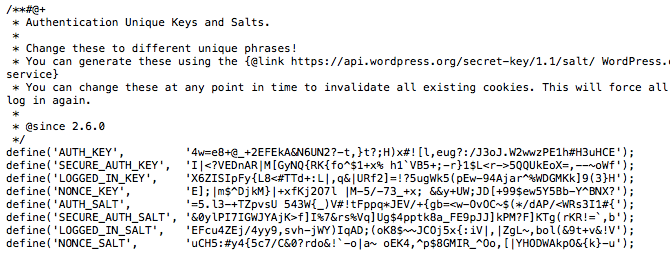
Essentially, these are random variables that are used to make it harder to guess or crack your WordPress passwords. This is because it adds an element of randomness to the way that passwords are stored in your database which makes them much harder to crack by brute force.
Although most self-hosted sites do not have these in place, you should actually implement them.
This is a relatively easy procedure:
1. Generate a set of keys using the WordPress random generator
2. Edit your wp.config file and in the Authentication Unique keys section you should find a place where to add the unique keys generated in step 1
Do not share or make these keys publicly available. It defeats their purpose.
#23: Disable PHP Execution
One of the first things a hacker would do if they got some kind of access to your site would be to execute PHP from within a directory. But if you were to disable this, even if a vulnerability existed on your WordPress website, this protection would seriously cripple the rest of a hacker’s attempts to takeover your site.
This is quite a strong WordPress security step and may break some themes and plugins that might require it, but you should implement this at least in the most vulnerable directories wp-includes and uploads.
This protection needs to be implemented via your .htaccess files. Add the below code to the .htaccess file in the root directory of your WordPress installation:
| <Files *.php> | |
| Order Allow, Deny | |
| Deny from all | |
| </Files> |
view rawdisable-php-execution hosted with ❤ by GitHub
#24: Segregate Your WordPress Databases
If you run multiple websites on the same hosting server account, you might be tempted to create all of the sites in the same database.
This creates a WordPress security risk. If one website gets compromised, all the other WordPress sites hosted on the same database are also at severe risk of hacking.
When setting up your WordPress installation, the first thing you should do is create a new database. Give it a separate database name, database user name and password, which is different from any other sites or logins you have.
This way, if one of your sites gets hacked the infection won’t spread to your other sites on the same shared hosting account.
#25: Restrict Database User Privileges
When setting up a WordPress site for the first time, you may, through lack of information, create a security issue via the database user privileges.
In general, the database user only needs the following privileges: For most WordPress day-to-day operations, the database user only needs data read and data write privileges to the database: SELECT, INSERT, UPDATE and DELETE.
You can thus remove additional privileges, such as DROP, ALTER and GRANT.
NB: Some major WordPress version upgrades might actually need these privileges, however in most cases the general running of WordPress doesn’t need these privileges.
It is advisable that before doing any WordPress updates, or installation or updates of WordPress plugins, you have a fully working backup.
#26: Disable File Editing
When you are in the initial phases of creating a website, you’ll probably need to tinker around with themes and plugin files. By default, WordPress administrators have the rights to edit PHP files.
Once your website has been developed and is live, you’ll have much less need to edit these files.
However, allowing administrators to edit files is a security issue. This is because if a hacker manages to login to your site, they’ll immediately have edit privileges and they’ll be able to change files to suit their malicious needs.
You can (and should) disable file editing for WordPress administrators after your website goes live through the following command in the wp-config.php file:
| define(‘DISALLOW_FILE_EDIT’, true); |
view rawdisable-file-editing hosted with ❤ by GitHub
#27: Secure Your wp-config.php File
If your WordPress files were to be analogous to the human body, the wp-config.php file would be the heart.
I won’t go into too much detail about wp-config.php here – we’ve already covered it quite extensively in The WordPress wp-config File: A Comprehensive Guide.
But the fact that it stores such important stuff such as the login details for the database used with your WordPress installation, hashing password salts and other important configuration settings, suffice to say this file is very important. Clearly, you don’t want anybody poking around this file.
I strongly recommend implementing specific security measures to safeguard this critical WordPress configuration file. There are disagreements about whether this file should be moved away from its root location, however, most agree this file must be secured.
If you haven’t already implemented step #23 above (Disable PHP Execution), then you can add the following to your .htaccess files:
| <files wp-config.php> | |
| order allow,deny | |
| deny from all | |
| </files> |
view rawsecure-wp-config hosted with ❤ by GitHub
#28: Disable XML-RPC (If You Aren’t Using It)
WordPress provides the ability for an application to access it remotely via what is known as an Application Programming Interface (or API). This means that applications can access your site (for benign reasons). A typical example of usage of the XML-RPC is if you are using a mobile application to update your site.
There are also some plugins, which use XML-RPC. For example, Jetpack uses XML-RPC functionality.
However, the XML-RPC can also be used to perform hack attacks on your website.
Many users today believe that XML-RPC is as secure as the rest of the WordPress core, but you can rest assured that XML-RPC is something that hacking scripts are going to be probing. You’ll probably find plenty of hits to XML-RPC if you have enabled logging on your site.
If you are sure that you don’t have any third party applications or no WordPress plugins are using your WordPress website via XML-RPC, you can choose to disable it using a WordPress plugin.
#29: Disable PHP Error Reporting
When you are developing a website, error reporting is a life-saver. It shows you exactly where an error is coming from so you can quickly fix it.
But, on a live site, error reporting gives crucial clues to hacker to make their life much easier than it has to be.
For example, check out the below error report:
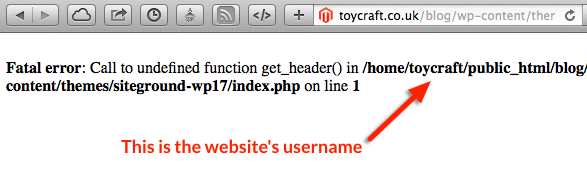
The error above is giving away the username of the account. That’s a crucial piece of information for somebody who is looking to attack your hosting account.
This is only one piece of information – error reporting can typically give really good clues if you know what weaknesses you are looking for.
You can disable PHP error reporting using the following change in your php.ini file:
| error_reporting = 4339 | |
| display_errors = Off | |
| display_startup_errors = Off | |
| log_errors = On | |
| error_log = /home/example.com/logs/php_error.log | |
| log_errors_max_len = 1024 | |
| ignore_repeated_errors = On | |
| ignore_repeated_source = Off | |
| html_errors = Off |
view rawdisable-php-error-reporting hosted with ❤ by GitHub
This ensures that any WordPress security risks created through exposure of sensitive information about your site are mitigated.
#30: Install a Firewall
There are two main types of firewalls, or uses for firewalls. In network security, firewalls are used to segregate different types of networks. Either keeping things from getting in, or things from getting out.
Again, if we use an analogy, a firewall can be described as a bouncer – you’re only allowed into a VIP party if you are on the guest list. Just like the bouncer at a party who typically stops people from getting in, software firewalls can be used to keep hackers from getting near your website(‘s party).
In the case of securing WordPress, we’re going to use a Web Application Firewall (WAF) to keep hackers from sticking their dirty little hands (or bots) into places where they don’t belong.
There are a number of WAF firewalls but one of the most reliable, free and open-source firewalls usually available with WordPress hosting services is the ModSecurity firewall.
You may want to ask your hosting service to see whether this is available on your hosting service, and enable it if it is. Once it is enabled, your hosting provider or your trusted WordPress developer can typically suggest or implement rules around ModSecurity.
#31: Use a Content Delivery Network Firewall
A Content Delivery Network’s primary use is typically to optimize the performance of your site by serving heavy resources fast. You can learn more CDNS in our article 9 Top CDN Services for a Super Fast WordPress Site.
CDNs, however, provide another secondary feature: most CDNs are able to protect against a number of WordPress security issues.
If you are using a CDN (and you should), make sure you are also enabling the security rules provided to improve the protection of your WordPress website.
#32: Monitor Your WordPress Security With Security Logging
If you don’t know what attacks are happening on your site, you’re hardly likely to be able to stop them, right?
You can improve your WordPress security through monitoring your logs. For example, if you find that most hacking attempts are coming from a specific country, perhaps one that your website doesn’t cater for, you could choose to use your firewall to block that country.
This is, of course, a very simple example of what monitoring can uncover.
You can choose to use OSSEC if you have direct access to your hosting server. You can also choose to use a security auditing plugin to keep regular audit logs.
Keeping WordPress Secure
This ultimate WordPress security checklist might give you a bunch of work if you haven’t much thought to securing your WordPress website before. The good thing is that these steps don’t require a lot of effort to become part of the process of creating a website.
WordPress security is something to be taken seriously. Hack attacks have become the norm. Your website is probably under attack right now.
OK, so you might not put all of the above in place, but the more of these WordPress security measures you put in place the better. Because wouldn’t you rather be safe than sorry?
How many of these steps have you taken to secure your WordPress site? Share your score below! And don’t forget to download our 32-step PDF checklist.
WordPress Security: The Ultimate 32-Step Checklist
Back when I was starting out as a web designer and developer, my biggest problem was getting stuff to work the way I wanted it to.
I was concerned more about getting things (mostly) working as I expected them to be. Getting things to look snazzy was usually one of my primary goals when finishing a website.
WordPress security was the least of my concerns. Hacking was something I read about, not something I expected to happen to me. SQL injection, cross-site scripting, elevation of privileges and critical security vulnerabilities were just buzzwords in tech news.
But one day, securing my sites suddenly got very important, very quickly when my Facebook feed told me there was a critical vulnerability in WordPress, which was actively being exploited. When I next tried to log in to my site, my credentials were not accepted.
Most of my sites had been compromised by the vulnerability.
I got lucky, though. I had taken one inadvertent precaution, which saved my sites from being fully exploited – I had renamed my admin username – and despite the fact the vulnerability had been exploited on my site, the hackers could not log in. I was using a complex administrator username rather than the default “admin” username the hackers were expecting.
Today I know different.
WordPress security is fundamental: Every WordPress website needs to be fully secured and hardened.
Secure your website with our ultimate 32-step security checklist for WordPress
Why Would a Hacker Be Interested In My Site?
Before actually diving deeply into securing your website and all of the steps you need to take to stop WordPress getting hacked, it’s crucial to understand the logistics and the reasoning behind a website hack.
It’s understandable that you might wonder:
“Why would a hacker be interested in my website? It’s just the website of my local business, seen by a few hundred people at most. What are they going to get out of it?”
There are many reasons why a hacker would be interested in your “small” website.
Although some hacking is done for political reasons (defacing of websites to send particular political messages, for example), these types of hacks are typically very localized and not as popular as the mainstream media would make them out to be.
Most hacking attacks happen for more devious reasons.
These days, hacking is part of a ring of criminality whose ultimate aim is to make money through fraudulent means. Typically, after a website is hacked it becomes a middle-man for the distribution of malicious software. Most times, the website owner is oblivious of all of this.
There are frameworks which are bought and sold in the online black market, making it dead-easy to distribute malware through hacked websites.
In essence, your website could become an involved party in criminal activity!
Besides that, there are other negative implications:
- Your site could be used as a spamming proxy
- A website that is hacked and defaced would most likely result in tarnishing of a brand’s reputation. That’s besides serious embarrassment
- Hacked sites typically overwhelm their hosting server, resulting in the closure of the site. This will typically result in loss of business
- The costs of recovering a hacked website can vary from very little (if you have a website backup) to a full redevelopment if your data is deleted/lost with no chance of recovery
Do you think your site is so small nobody will attack it? Think again.
Using the following WordPress security checklist will go a long way towards making your WordPress site hacker-proof.
How Does a Hacker Find My Site?
You might falsely assume that in the millions of websites available online, the likelihood of a hacker finding and targeting your site is extremely remote. After all, your site is only a drop in an ocean of websites, right?
You’re horribly wrong.
Hackers don’t do this work manually. They employ minions to do their dirty work.
Well, not really minions – they’re actually (ro)bots, or programs whose sole purpose is to seek out vulnerable websites.
These programs or scripts are typically run on cloud servers, where they can be setup and destroyed at will leaving little to no traces. The scripts employ means to discover hundreds if not thousands of websites per hour.
The fact that the scripts are bought very cheaply and run on cheap cloud hosting servers make the “investment” worthwhile. These scripts are commonly bought and sold on dodgy marketing forums.
Once a site is found, it is probed for thousands of known vulnerabilities. If your WordPress site has not been fully secured, the likelihood of the site emerging unscathed is absolutely minimal.
Vulnerabilities are continuously being discovered in WordPress and its plugins. That’s why securing WordPress is critical to the health of your website.
Securing WordPress: A 32-Step Checklist
With all of the above scary stuff in mind, I want to make sure that you’re armed with all the knowledge you can get to fully secure your WordPress website.
Here’s a checklist of ALL the things you should be doing to secure your WordPress sites.
This checklist is split into two: The first part includes measures absolutely everybody should be doing – mostly basics stuff, like having strong passwords. The second part goes into advanced measures for WordPress security for those who are really paranoid about security. This is for admins who want to lock the door, put a chain around the door, and put a padlock on it. And then a padlock on the padlock.
Part 1: The Steps Everybody Should Take to Secure Their WordPress Website
#1: ALWAYS Keep Your Version of WordPress Up-To-Date
#2: Don’t Change WordPress Core
#3: Make Sure All Your Plugins Are Updated
#4: Remove Any Inactive or Unused Plugins
#5: Make Sure All Themes Are Kept Updated
#6: Install Themes, Plugins and Scripts ONLY From Their Official Source
#7: Choose a Secure WordPress Hosting Service
#8: Make Sure Your Site is Running the Latest Version of PHP
#10: Always Use Strong Passwords
#12: Protect Your Password(s) By Avoiding Plain-Text Password Transmission
#13: Only Update Your Site From Trusted Networks
#15: Enable Google Search Console
#16: Secure WordPress With a Bulletproof WordPress Security Plugin
#17: If All Else Fails, Restore From Backup
Part 2: Securing a WordPress Website for Security Freaks
Well, not really security freaks, per se.
Although these are slightly more advanced WordPress security tips, you typically only need to know how to install a plugin, tweak a few files here and there and in general be ready for the possibility to break stuff. Be ready to revert with backups if that happens.
#19: Enable Two-Factor Authentication
#20: Ensure File Permissions Are Correct
#21: Change the Default Table Prefix
#22: Ensure You’ve Set WordPress Secret Authentication Keys
#24: Segregate Your WordPress Databases
#25: Restrict Database User Privileges
#27: Secure Your wp-config.php File
#28: Disable XML-RPC (If You Aren’t Using It)
#29: Disable PHP Error Reporting
#31: Use a Content Delivery Network Firewall
#32: Monitor Your WordPress Security With Security Logging
Part 1: The Steps Everybody Should Take to Secure Their WordPress Website
#1: ALWAYS Keep Your Version of WordPress Up-To-Date
Time and again, you hear of people who disable WordPress core updates because “an update might break one of my plugins.”
This is seriously flawed reasoning.
If you had to choose between a hacked site and a temporarily broken plugin, which would you choose?
Plugins that are incompatible with the latest versions of WordPress are only going to stay that way for a very short time. A hacked site, on the other hand, is a far bigger problem.
Each core update fixes any recently discovered security problems. If your WordPress core software is not updated, your website will be vulnerable to these problems.
If you want to enable WordPress core updates without a plugin you can do it through your wp.config.php file. Add the following line to the file:
| define(‘WP_AUTO_UPDATE_CORE’, true); |
view rawwordpress-auto-updates hosted with ❤ by GitHub
The above, however, will also enable core development and nightly updates, which you probably don’t want. Add the following to your functions.php file to only get major and minor releases:
| add_filter( ‘allow_dev_auto_core_updates’, ‘__return_false’ ); |
view rawwordpress-minor-updates hosted with ❤ by GitHub
Note: We don’t usually recommend directly editing your functions.php file. It’s always better to create a child theme.
We will discuss later on how to also automatically update WordPress plugins and WordPress themes.
#2: Don’t Change WordPress Core
The moment you or a developer edits WordPress core source files, you can no longer easily and automatically update WordPress to the latest version since you’ll lose changes you made to your site
This leaves your website dead in the water as soon as a security vulnerability is discovered in your version of WordPress. You’ll either have to figure out how to implement the specific fixes yourself, or just leave it unpatched. The former is a lot of hassle and a logistical nightmare; the latter is a serious security risk.
What should you do if you need to change WordPress functionality? Write a plugin of course. This gives you the ability to do whatever you need without compromising WordPress core.
Of course, the same logic applies to plugins and themes. The moment you perform any core tweaking of plugins and themes you lose the ability to update to the latest version. This leaves your site open to hacking.
There are ways and means of getting the desired functionality you need without actually changing the core. If any developer you work with suggests making any such changes, run a mile.
#3: Make Sure All Your Plugins Are Updated
As with WordPress core files, vulnerabilities are frequently found in third party WordPress plugins. There have been plenty of high-profile hacking incidents due to popular plugins containing vulnerabilities.
We won’t name and shame them here. Most software is prone to these issues at some point in its existence. It’s how the vulnerability is dealt with that shows you what the people running the company are made of.
Many times, as soon as a problem is discovered the developers of the plugin will quickly fix it and release an update.
At that point, it becomes your responsibility to update the plugin to the latest version otherwise you are still prone to a hack attack.
Always keep your plugins up-to-date to ensure you are using the latest version.
Whether you do it manually, or automatically, always keep your plugins updated.
You can enable automatic background updates on WordPress.org plugins using the following change in your functions.php file
| add_filter( ‘auto_update_plugin’, ‘__return_true’ ); |
view rawauto-update-wordpress-plugins hosted with ❤ by GitHub
This only applies to plugins downloaded from WordPress.org. Any commercial plugin updates need to be handled through their own update mechanism.
Don’t neglect the updating of plugins. Keep memberships of plugins active so that you can always get the latest updates.
#4: Remove Any Inactive or Unused Plugins
As the number of plugins you install increases, so do the risks of a vulnerability being discovered in one of those plugins.
Sometimes we install plugins to test their functionality and then forget to remove them from our site. If a vulnerability is discovered in these plugins, your site becomes a sitting duck (especially if you don’t follow the advice above and always update the plugins).
Your website is still vulnerable even if that plugin is installed on your website and not being used.
The safest way to minimize the risks is to completely uninstall any plugins you are not using. There is a very easy way to know which plugins are not being used. They are marked as Inactive in the Plugin section of the WordPress admin.
Delete them.
Also, remove any plugins that are active but still not actually being used. Better still, when testing plugins, don’t test them on your live site. Instead, create a test copy of your site (on a local test server or somewhere that is segregated from your live server). Perform any plugin testing on that site instead of your live site.
#5: Make Sure All Themes Are Kept Updated
The same logic that applies to WordPress core updates and plugin updates, applies to themes. Securing WordPress means that all themes need to be kept updated to their latest versions. Otherwise, any security holes that have been fixed will remain an issue on your site.
Now you may probably be thinking about all of the changes you’ve done to the theme and how these will break if you perform a theme update. In reality, changes to themes should be done via child themes, rather than directly to the actual theme. This will allow you to get the latest fixes and security updates without breaking your changes.
If you want to put your mind completely at rest, it would be best to also remove any unused themes. You can check which themes requiring updates from the Appearance > Themes section in the WordPress admin.
You can also enable automatic background updates for WordPress.org themes also using the following change in your functions.php file:
| add_filter( ‘auto_update_theme’, ‘__return_true’ ); |
view rawauto-update-wordpress-themes hosted with ❤ by GitHub
This applies to themes downloaded from WordPress.org.
Any commercial theme updates need to be handled through their own update mechanism. Keep your subscriptions active to ensure you get all security updates.
Note: If tweaking wp-config.php and functions.php files is not your thing, you may choose to enable all automatic background updates using the WordPress plugin, Advanced Automatic Updates. You can use Advanced Automatic Updates to tweak the settings of auto-updates and ENABLE all of the above.
#6: Install Themes, Plugins and Scripts ONLY From Their Official Source
Sometimes when times are tough we might get tempted to “bypass” the payment of a good theme or plugin, by getting it from *cough* less than reputable sites.
Actually, there’s no harm in naming and shaming here. Pirating, torrenting and other warez sites are something you need to avoid like the plague.
What we typically don’t realize, though, is that many of these pirated themes you download for free have been maliciously tweaked. Most times a back door has been installed in the script. This allows the site where the theme or plugin is used to be remotely controlled by hackers for nefarious reasons.
Would you trust your money to a known scam artist? I wouldn’t think so. Same thing for your website. Don’t trust “free” WordPress scripts coming from people whose business is stealing other people’s work.
So where are the safe sites to go to find quality themes?
WordPress.org is the most common place where plugins and themes for WordPress are found. Commercial plugins or themes can be found at many sites starting of course with WPMU DEV and sites like WordPress.com, ThemeForest.net or CodeCanyon.net
If WordPress security is important to you, stay away from pirate sites.
#7: Choose a Secure WordPress Hosting Service
A good WordPress hosting service goes a long way towards protecting your site from hacking attacks.
Security conscious hosting services will have a dedicated security team who monitor the latest vulnerabilities (even 0-day hacks, i.e. those for which there is no remedy yet) and preemptively apply rules on their firewalls to mitigate any hack attacks on your site.
WordPress hosting is a bit of a hot topic, so I won’t be making recommendations here, but the WordPress hosting page does make a few suggestions. These are by no means the only security conscious hosting companies out there. Check out post Web Hosting Review: So Just Who is the Best? for a rundown on the web hosts to look out for.
#8: Make Sure Your Site is Running the Latest Version of PHP
The global WordPress statistics page includes an alarming statistic: Only 1.7% of WordPress installations run on the latest version of PHP (7), whilst about 19.8% run version 5.6, which is still supported.
The rest of the WordPress installations (close to 80%) run on versions that are no longer supported!
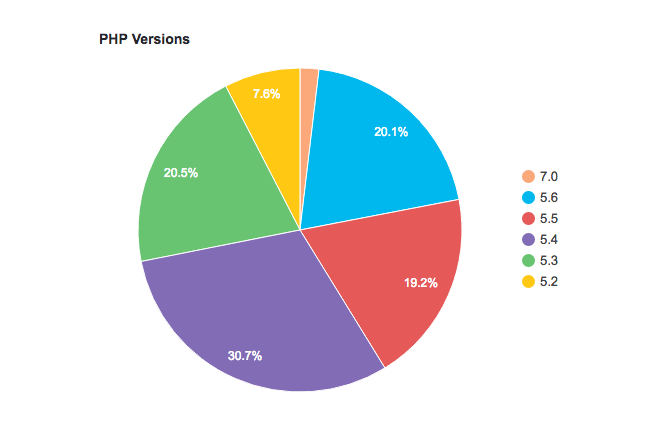
Besides the fact your site is not benefiting from performance features released with latest versions, it also means that security fixes that are discovered will not be fixed. They will remain in the wild, ready for exploitation.
Just like WordPress gets a number of core updates, including security fixes, PHP, the underlying engine of WordPress, also gets it fair share of version updates.
Now, updating WordPress core, themes and plugins is a fairly straightforward operation.
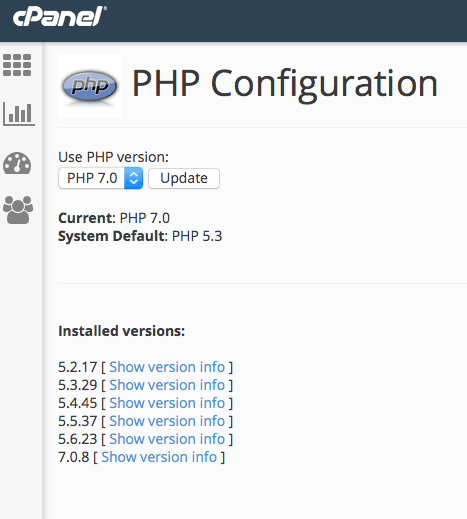
Don’t forget to update to the latest version of PHP.
On the other hand, updating your PHP version depends largely on your hosting service. A good hosting service should make the latest PHP versions available for use with your WordPress installation through something called with PHP Version Switcher (which is typically accessed through your cPanel account).
#9: Change the Admin Username
Up until WordPress 3.0, the default user name of the administrator login was “admin.” This created a bit of a bonanza for hackers as there was no need for them to guess the administrator username. This is something still valid today. Many people still choose to use “admin” as the default administrator user name.
One of the quickest ways to secure your WordPress admin login against brute force attacks is to change the default “admin” username to something more difficult to guess. (This is what saved my own site from getting hacked).
You can – and should – do this during the actual installation of WordPress.
If your username is currently admin, you should create a new administrator user with a username that is less obvious to guess and delete the old admin user.
You can also rename the user using phpMyAdmin, or choose to run a SQL script on your database to rename the admin user:
| UPDATE wp_users SET user_login = ‘newcomplexusernameforadmin’ WHERE user_login = ‘admin’ |
view rawupdate-admin-username hosted with ❤ by GitHub
This quick and easy WordPress security trick can thwart many simple hacking attempts.
#10: Always Use Strong Passwords
When watching a client enter their administrator password, I like to give them their privacy and look away from the keyboard.
But a few years back, I accidentally didn’t look away fast enough whilst they were typing the password. To my dismay, I saw them type the following:
1 2 3 4 5 6
To say I was horrified would be an understatement.
Another login and password combination I come across very often, which (nearly) brings tears to my eyes, is this username and password combination:
admin/admin
Besides the fact that anybody looking over your shoulder (like myself) would immediately pick up that password, there is a much more serious reason why you must create strong passwords: hackers know that human beings tend to forget their passwords and are prone to using simple, easy to guess passwords.
They use this to their advantage by having a list of most commonly used passwords, which they try over and over again. This is called brute-forcing a password. Since some people WILL use these passwords, it’s essentially a numbers game – and the odds are usually stacked against you.
So always use a strong password.
Here’s an example of a strong password: ThizzI5alongstr*ngbuzzw00rd$
Should all your passwords be as complex as this one? Probably.
#11: Don’t Reuse Passwords
You should NEVER reuse passwords.
I hear you, it’s convenient to have one (hopefully strong) password across the board. You won’t have to remember so many passwords but this is very wrong on many levels.
Once again, hackers know this is a bit of a human weakness. It means that when one of your accounts is compromised they have probable access to ALL of the rest of your accounts.
There are plenty of password managers out there that will allow you to create different passwords and store them securely. These are highly recommended.
This is not just WordPress security – this is just common sense.
#12: Protect Your Password(s) By Avoiding Plain-Text Password Transmission
It’s a known fact (and a sad reality) that there is all kinds of snooping on internet traffic. Sensitive data such as credit cards and passwords should never be sent in unencrypted form.
There will be plenty of eyes (and analyzers) on your data. Do make sure you protect your passwords by employing the following preventive techniques
- Don’t send passwords over email, chat, social networks or other unencrypted forms of transmission
- Implement HTTPS on your WordPress site, particularly on your backend, to avoid passwords being sent in plain-text. You can learn all about implementing HTTPS in our article How to Use SSL and HTTPS with WordPress.
- Avoid using plain FTP when accessing your site. Use SSH or FTPS. The FTP protocol was written in the internet dark ages, and it’s not safe to use. Passwords and files are transmitted in plain text and not encrypted at all. FTPS or (Secure FTP), on the other hand, actually encrypts data transmission over FTP. You’ll need to setup an FTPS account on your hosting server before being able to do this.
- Of course, passwords should not be shared between users or stored in plain-text anywhere no matter how convenient this may be. The practice of sharing logins and passwords flies in the face of security and accountability.
#13: Only Update Your Site From Trusted Networks
Sometimes we tend to take the convenience of finding free Internet Wifi as a godsend.
But paranoid security freaks (like me) tend to shudder at the thought of updating a website from an untrusted network such as the free Wifi connection at your local cafe.
An open Wifi connection is extremely easy to snoop on. You may be getting much more than the “freebie” you thought you were getting if you access your WordPress administration site from a network that is untrusted.
Only update your site from trusted networks, such as those at your home and at your office.
#14: Use a Local Anti-Virus
Imagine you are a computer virus sitting on a desktop workstation. Bear with me for a moment.
Remember that a virus’ primary aim is to spread itself as far and wide as possible. What better way for that virus to propagate than replicating itself onto your website. That’s pretty nifty, huh?
This is a tactic widely used by viruses. There are many infected workstations out there at any point in time. And of those workstations, there are many who are being used by WordPress administrators.
That’s a bit of a worst case combination. A virus on your desktop can quickly spread itself and lead to infection of your site too. It can also snoop on your passwords and, heck, even your credit card and other personal details.
Make sure your local workstation is running a good and updated antivirus to prevent it from getting infected and spreading to your website.
#15: Enable Google Search Console
Whilst this is not a strict WordPress security recommendation, it’s something that can supplement the steps you’ve already taken to bolster your WordPress security.
Google and other search engines have an interest in making sure your website is kept clean of malware. For this reason, the Google Search console will advise you if your website starts to host any malicious files.
Although this is a non-ideal situation where your site would have been hacked already, rather than acting to prevent your WordPress site from being hacked, it’s still good to know that malware has been detected on your site so that you can rectify the problem as soon as possible.
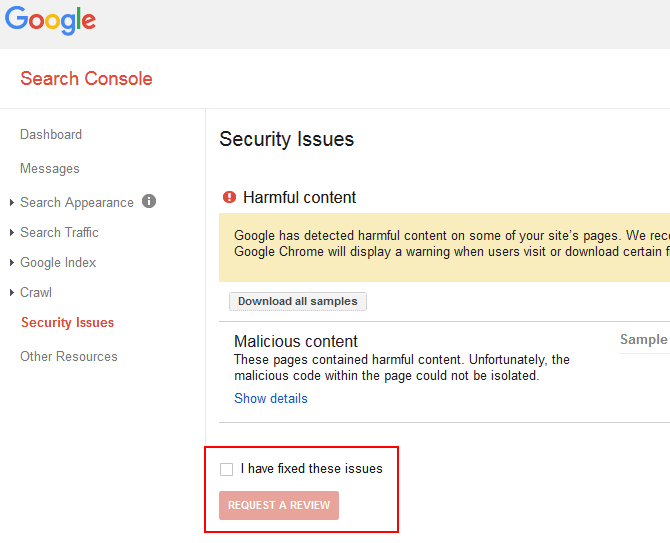
#16: Secure WordPress With a Bulletproof WordPress Security Plugin
Many of the steps in this checklist are not trivial. They also might require a bit of technical tinkering with your WordPress website, and rather than securing WordPress, you may blow it up.
We’ve got you covered, though. Defender is an easy but sure way of securing WordPress with little to no effort from your side. Our security plugin can identify any WordPress security issues currently affecting your websites and provide guidance on how to fix them.
Whilst, we believe that Defender is one of the best options for people familiar with WPMUDEV, there are plenty of other options in terms of WordPress security. Two of the more popular options are Sucuri and Wordfence – they are very different in the way that they work. The former is a fully cloud-based solution which also couples as a firewall and even a CDN, the latter is actually working on your site directly (it’s a plugin). We’ve reviewed both of them on CollectiveRay.com, so have a look at that article too, if you want to make an informed choice with the pros and cons of each.
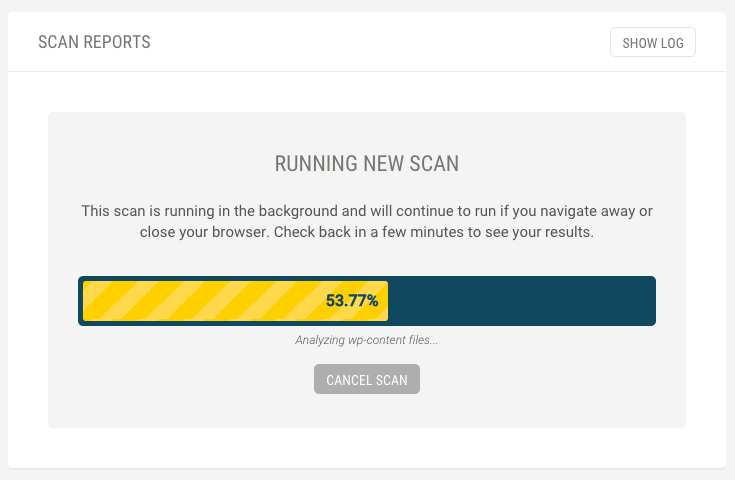
Once you’ve fixed any issues, you can also run a scan to ensure that none of your themes or plugins contain any known vulnerabilities. If they do, you’ll be able to take action to fix these issues before they become major problems for your site.
Besides the first time you install it, Defender allows you to schedule regular scans of your websites. If you’re like me, you’re bound to be very enthusiastic about WordPress security one day, but as things get busy security goes on to the backburner. Automatic scans will ensure you don’t go lax with your WordPress security.
There are plenty of other excellent features in WordPress Defender, including blacklist monitoring and alerts, vulnerability reports and customized hardening.
#17: If All Else Fails, Restore From Backup
I’ve listed quite the checklist of things you should do to secure WordPress and I do understand that it may be somewhat tasking to implement all of these. I also know that in practice, you might lapse and miss a few of them.
But there’s one task you really should not skip!
If your timing is unfortunate and your lapse happens at the same time as a hack attack, it’s important o have a fall-back plan.
The one thing you should never, ever miss or forget to do is have a WordPress backup plan. Not only in the case of hack attacks, but even in the case of accidents, technical faults and other mishaps. Having a backup ensures you can get your site back up and running again quickly.
Snapshot Pro is like a time machine for your website, enabling you to backup and restore your entire site and even schedule regular automated backups.
Once you’ve setup a backup plan, you know that if your site is hacked you just need to discover the source of the hack, revert from backup, fix the “hole” that allowed your site to get hacked and you’re good to go.
Important note: You should TEST your WordPress backup every so often by restoring it to a temporary location and making sure everything is in working order. The last thing you need is a backup that you think works, but in fact doesn’t.

Part 2: WordPress Security For Security Freaks
#18: Limit Login Attempts
We’ve already discussed brute-forcing of passwords and the fact that using bots is cheap and a good investment for hackers. For this reason, you should put in place mechanisms to block any attempts at brute-forcing your password.
The Limit Login WordPress plugin does exactly this. If it detects a number of incorrect login attempts it denies that user the possibility of trying again for some time. This, of course, makes the brute-forcing attempts much more difficult to succeed and significantly improves your WordPress security.
#19: Enable Two-Factor Authentication
One way of quickly and very easily securing your WordPress logins is by enabling Two Factor Authentication, also known as 2FA.
2FA creates a mechanism whereby to log in to your WordPress backend, besides your regular password, you will also need a time-based security token that is unique to each user. This token also expires after a period of time usually 60 seconds.
The security token is typically generated by an app such as the Google Authenticator.
Because there is a security token unique to each single user that expires, even if somebody knows your login credentials, they will still not be able to log in. This is because they will not have the current security token. This drastically increases the strength of your login and also helps mitigate brute force attacks on your login details.
There are a number of plugins that can help you setup WordPress Two Factor Authentication. Check out 6 Best WordPress Security Authentication Plugins for some of our favorites.
#20: Ensure File Permissions Are Correct
This is a bit of technical thing.
PHP and WordPress in general use a set of permissions associated with files and folders. Without going into too much detail, there are different types of permissions
- Publicly writable files and directories
- Files writable by the web server only
- Read-only files
In general, your web server typically needs to be able to write files for WordPress to work correctly, whilst the public internet NEVER needs to have write access to your files.
Some newbie or lazy developers, might suggest that you change permissions to be more lax. For example, they might suggest making certain files or folders publicly writeable (777). This will create a serious security threat because it means that anyone can write anything to that folder. You can rest assured that you’ll find plenty of nasties in your WordPress site if you do that. They will also probably find ways and means of jumping out of the folder to wreak havoc on the rest of your site.
As a general rule of thumb, files should have a 644 permission and folders should have 755 permissions. The wp-config.php file should have 400 or 440 permission.
If anybody tells you otherwise, be very wary. My suggestion is stop dealing with anybody who suggests otherwise.
How can you check for the correct file permissions? Defender, mentioned above, is a WordPress security plugin that will check and fix file permissions for you as necessary.
#21: Change the Default Table Prefix
This is another remnant of old versions of WordPress. Previously, the name of WordPress tables in the database used to start with the prefix wp_
Although this is no longer default behavior, some people still tend to revert to this (unsafe) practice, whilst older versions of course still have to live with this.
Although this is, strictly speaking, WordPress security through obscurity, renaming the tables from wp_ to a different prefix may still block some attempted SQL injection attacks.
The procedure to rename existing wp_ tables should be done only by your trusted WordPress developer.
#22: Ensure You’ve Set WordPress Secret Authentication Keys
You might have come across these eight WordPress security and authentication keys in your wp-config.php file and wondered what they are. You may also have never seen or heard about them.
They look something like this:
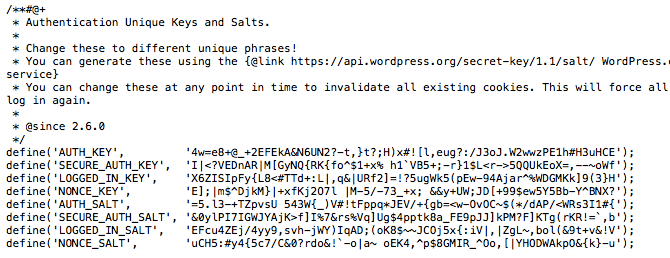
Essentially, these are random variables that are used to make it harder to guess or crack your WordPress passwords. This is because it adds an element of randomness to the way that passwords are stored in your database which makes them much harder to crack by brute force.
Although most self-hosted sites do not have these in place, you should actually implement them.
This is a relatively easy procedure:
1. Generate a set of keys using the WordPress random generator
2. Edit your wp.config file and in the Authentication Unique keys section you should find a place where to add the unique keys generated in step 1
Do not share or make these keys publicly available. It defeats their purpose.
#23: Disable PHP Execution
One of the first things a hacker would do if they got some kind of access to your site would be to execute PHP from within a directory. But if you were to disable this, even if a vulnerability existed on your WordPress website, this protection would seriously cripple the rest of a hacker’s attempts to takeover your site.
This is quite a strong WordPress security step and may break some themes and plugins that might require it, but you should implement this at least in the most vulnerable directories wp-includes and uploads.
This protection needs to be implemented via your .htaccess files. Add the below code to the .htaccess file in the root directory of your WordPress installation:
| <Files *.php> | |
| Order Allow, Deny | |
| Deny from all | |
| </Files> |
view rawdisable-php-execution hosted with ❤ by GitHub
#24: Segregate Your WordPress Databases
If you run multiple websites on the same hosting server account, you might be tempted to create all of the sites in the same database.
This creates a WordPress security risk. If one website gets compromised, all the other WordPress sites hosted on the same database are also at severe risk of hacking.
When setting up your WordPress installation, the first thing you should do is create a new database. Give it a separate database name, database user name and password, which is different from any other sites or logins you have.
This way, if one of your sites gets hacked the infection won’t spread to your other sites on the same shared hosting account.
#25: Restrict Database User Privileges
When setting up a WordPress site for the first time, you may, through lack of information, create a security issue via the database user privileges.
In general, the database user only needs the following privileges: For most WordPress day-to-day operations, the database user only needs data read and data write privileges to the database: SELECT, INSERT, UPDATE and DELETE.
You can thus remove additional privileges, such as DROP, ALTER and GRANT.
NB: Some major WordPress version upgrades might actually need these privileges, however in most cases the general running of WordPress doesn’t need these privileges.
It is advisable that before doing any WordPress updates, or installation or updates of WordPress plugins, you have a fully working backup.
#26: Disable File Editing
When you are in the initial phases of creating a website, you’ll probably need to tinker around with themes and plugin files. By default, WordPress administrators have the rights to edit PHP files.
Once your website has been developed and is live, you’ll have much less need to edit these files.
However, allowing administrators to edit files is a security issue. This is because if a hacker manages to login to your site, they’ll immediately have edit privileges and they’ll be able to change files to suit their malicious needs.
You can (and should) disable file editing for WordPress administrators after your website goes live through the following command in the wp-config.php file:
| define(‘DISALLOW_FILE_EDIT’, true); |
view rawdisable-file-editing hosted with ❤ by GitHub
#27: Secure Your wp-config.php File
If your WordPress files were to be analogous to the human body, the wp-config.php file would be the heart.
I won’t go into too much detail about wp-config.php here – we’ve already covered it quite extensively in The WordPress wp-config File: A Comprehensive Guide.
But the fact that it stores such important stuff such as the login details for the database used with your WordPress installation, hashing password salts and other important configuration settings, suffice to say this file is very important. Clearly, you don’t want anybody poking around this file.
I strongly recommend implementing specific security measures to safeguard this critical WordPress configuration file. There are disagreements about whether this file should be moved away from its root location, however, most agree this file must be secured.
If you haven’t already implemented step #23 above (Disable PHP Execution), then you can add the following to your .htaccess files:
| <files wp-config.php> | |
| order allow,deny | |
| deny from all | |
| </files> |
view rawsecure-wp-config hosted with ❤ by GitHub
#28: Disable XML-RPC (If You Aren’t Using It)
WordPress provides the ability for an application to access it remotely via what is known as an Application Programming Interface (or API). This means that applications can access your site (for benign reasons). A typical example of usage of the XML-RPC is if you are using a mobile application to update your site.
There are also some plugins, which use XML-RPC. For example, Jetpack uses XML-RPC functionality.
However, the XML-RPC can also be used to perform hack attacks on your website.
Many users today believe that XML-RPC is as secure as the rest of the WordPress core, but you can rest assured that XML-RPC is something that hacking scripts are going to be probing. You’ll probably find plenty of hits to XML-RPC if you have enabled logging on your site.
If you are sure that you don’t have any third party applications or no WordPress plugins are using your WordPress website via XML-RPC, you can choose to disable it using a WordPress plugin.
#29: Disable PHP Error Reporting
When you are developing a website, error reporting is a life-saver. It shows you exactly where an error is coming from so you can quickly fix it.
But, on a live site, error reporting gives crucial clues to hacker to make their life much easier than it has to be.
For example, check out the below error report:
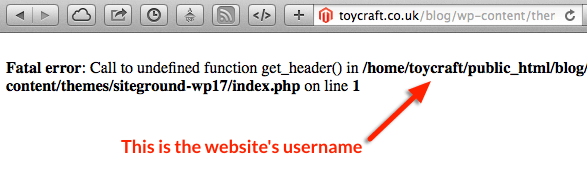
The error above is giving away the username of the account. That’s a crucial piece of information for somebody who is looking to attack your hosting account.
This is only one piece of information – error reporting can typically give really good clues if you know what weaknesses you are looking for.
You can disable PHP error reporting using the following change in your php.ini file:
| error_reporting = 4339 | |
| display_errors = Off | |
| display_startup_errors = Off | |
| log_errors = On | |
| error_log = /home/example.com/logs/php_error.log | |
| log_errors_max_len = 1024 | |
| ignore_repeated_errors = On | |
| ignore_repeated_source = Off | |
| html_errors = Off |
view rawdisable-php-error-reporting hosted with ❤ by GitHub
This ensures that any WordPress security risks created through exposure of sensitive information about your site are mitigated.
#30: Install a Firewall
There are two main types of firewalls, or uses for firewalls. In network security, firewalls are used to segregate different types of networks. Either keeping things from getting in, or things from getting out.
Again, if we use an analogy, a firewall can be described as a bouncer – you’re only allowed into a VIP party if you are on the guest list. Just like the bouncer at a party who typically stops people from getting in, software firewalls can be used to keep hackers from getting near your website(‘s party).
In the case of securing WordPress, we’re going to use a Web Application Firewall (WAF) to keep hackers from sticking their dirty little hands (or bots) into places where they don’t belong.
There are a number of WAF firewalls but one of the most reliable, free and open-source firewalls usually available with WordPress hosting services is the ModSecurity firewall.
You may want to ask your hosting service to see whether this is available on your hosting service, and enable it if it is. Once it is enabled, your hosting provider or your trusted WordPress developer can typically suggest or implement rules around ModSecurity.
#31: Use a Content Delivery Network Firewall
A Content Delivery Network’s primary use is typically to optimize the performance of your site by serving heavy resources fast. You can learn more CDNS in our article 9 Top CDN Services for a Super Fast WordPress Site.
CDNs, however, provide another secondary feature: most CDNs are able to protect against a number of WordPress security issues.
If you are using a CDN (and you should), make sure you are also enabling the security rules provided to improve the protection of your WordPress website.
#32: Monitor Your WordPress Security With Security Logging
If you don’t know what attacks are happening on your site, you’re hardly likely to be able to stop them, right?
You can improve your WordPress security through monitoring your logs. For example, if you find that most hacking attempts are coming from a specific country, perhaps one that your website doesn’t cater for, you could choose to use your firewall to block that country.
This is, of course, a very simple example of what monitoring can uncover.
You can choose to use OSSEC if you have direct access to your hosting server. You can also choose to use a security auditing plugin to keep regular audit logs.
Keeping WordPress Secure
This ultimate WordPress security checklist might give you a bunch of work if you haven’t much thought to securing your WordPress website before. The good thing is that these steps don’t require a lot of effort to become part of the process of creating a website.
WordPress security is something to be taken seriously. Hack attacks have become the norm. Your website is probably under attack right now.
OK, so you might not put all of the above in place, but the more of these WordPress security measures you put in place the better. Because wouldn’t you rather be safe than sorry?
How many of these steps have you taken to secure your WordPress site? Share your score below! And don’t forget to download our 32-step PDF checklist.